PrintNightmare Zero-Day Remote Code Execution Vulnerability
Microsoft has introduced the methods of combating the zero-day vulnerability for the Print Spooler service of Windows, also known as PrintNightmare, which has been newly detected and has not yet been released with an official patch and solution. With this method it is possible to prevent attacks that targeted the Windows Print service and against the systems carry this vulnerability.

It is known that this remote code execution vulnerability is watched with the 2021-34527 code and affects all windows versions. For all that**,** Microsoft is still investigating about this vulnerability can be exploited on all Windows operating systems.

This vulnerability known as CVE-2021-34527 gives attackers remote code execution authorization with user authorization and so it gives remote software installation, viewing, modification or deletion or define user with admin authority possibilities.
Microsoft has released a new security advisory about PrintNightmare, which is still up-to-date and known to be exploited. However, it didn’t make a statement about who exploited the vulnerability and who is behind it.

So far, there is no any official security patch for preventing this vulnerability. Because, Microsoft’s research and elimination studies are still on going.
Microsoft also released a statement in response to the confusion of PrintNightmare with a bug similar to this and addressed as CVE-2021-1675 and was released a patch for it in June 2021.
Korunma Yöntemleri

Firs of all, security updates dated 8 June must be applied on all Windows systems.
Although Windows has not yet release an official patch for eliminating this vulnerability, still shared some advises to prevent this vulnerability from being exploited and thus attackers from hijacking systems.
According to this, Print Spooler service of Windows can be disabled , printing function can be removed both local and on the net. Or because of Group Policy remote printing requests to the server or computer can be blocked and thus attack surface can be eliminated. According to Microsoft when the second option chosen system no longer will function as a print server but it will be possible to print from printers attached itself directly (direct attach).

According to this one of the below should be applied:
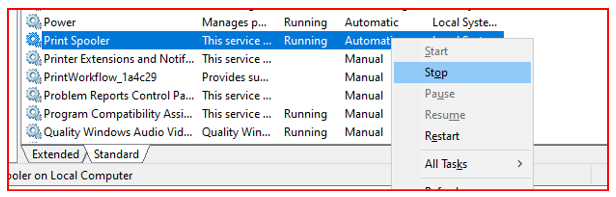
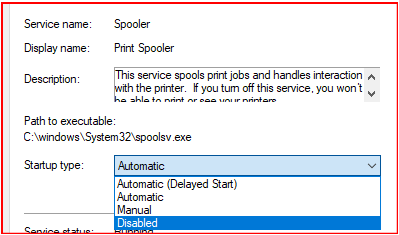
Option - 1 : Stopping the Print Spooler service
You can stop Windows’s Print Spooler service form graphic interface (stop) and then disable the startup state (disabled).
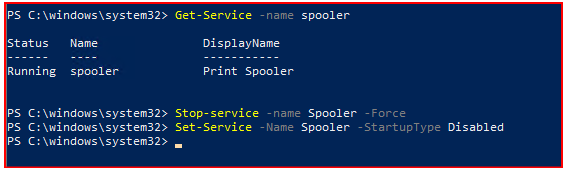
Or you can do this via PowerShell with admin authorization as follows:
Option - 2 : Blocking The Incoming Remote Printing Function with Group Policy
If you want to continue to print from direct attached printers to the computer instead of completely stopping the printing service, in this case on the Group Policy
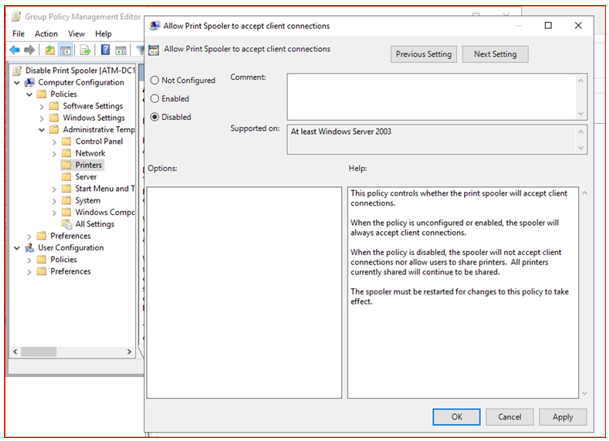
by selecting Computer Configuration / Administrative Templates / Printers,
Set “Allow Print Spooler to accept client connections:” setting “disable”

- Turn Back
- 4 min reading