
Conti Malicious Software Activities Is Increasing
Conti ransomware group which disrupted the health systems and emergency services of many countries have affected more then 400 systems globally and it still continues to disrupt the health systems, emergency services and municipality services.

Conti group encrypts data and demand ransom like a standard ransomware malicious group either, if the payment is not done in particular time it is ensured that the institution is reduced to legal and reputational distress by revealing the data by this group. Conti group determines the prices according to the system they infiltrated and finally they demanded 25 million Dolars from a health system of a country.

Groups that bought stolen RDP user accounts are starting to face ransom attacks in institutions, and it is seen that different groups with the same information also corrupt many files during encryption within the institution.

In addition it is stated that the reason ransom groups choose mostly health, energy, telecom, defense such sectors, is even the implementation of the defense and contingency plan in many organizations takes longer than paying the ransom and activating the systems.
It has detected that the USA industrial company BlueForce has affected from a ransomware and critical datas belong to BlueForce have leaked. The attack, emerged when screenshots of user’s messages trying to connect with Conti ransomware group were shared on the forums.
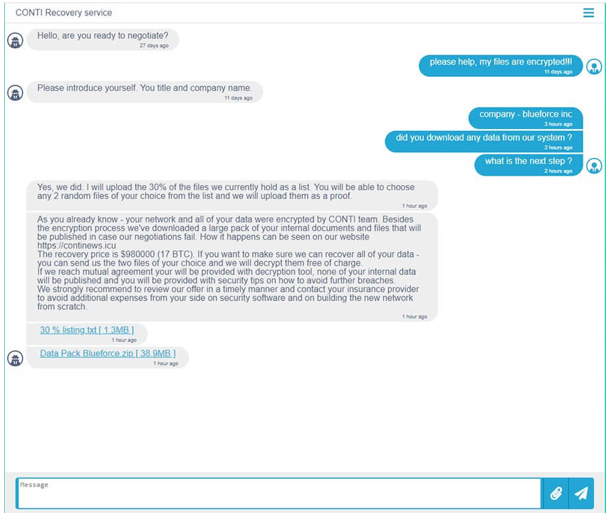
The malicious software, infects the target devices with 200kb DLL files that includes Cobalt Strike shell. After it has accessed, communicate with the C&C (Command and Control) server and makes system exploration. Conti malicious which encrypts the critical files in the target device, delivers the encrypted files to C&C server. Threat actors behind Conti ransomware, tells that they will give back the captured datas with 17 BTC (976,577.82 $).

Security researchers state that threat actors behind Conti ransomware use advanced ways. In order not to affect by critical cyber attacks, it is recommended that not to download files from insecure sources and not to block Ioc (Indicator of Compromise) detected below indications by security devices.
- Turn Back
- 3 min reading
-
Securvent